SEND US A MESSAGE
CONTACT INFORMATION

We provide unlimited support for our customers. We try to reply for all your messages as soon as possible!
When your WordPress site is compromised, the warning signs can vary, but here are the most common red flags:
These symptoms don’t just frustrate site owners – they also damage trust with visitors and hurt your SEO rankings. Left unchecked, malware infections often result in Google delisting or browser warnings that prevent users from visiting your site.
Use Antivirus and Security Plugins. The first line of defense against malware is a strong security plugin.
Wordfence Security: Scans all theme and plugin files for unauthorized modifications, detects anomalies in PHP and JS code, and blocks malicious IPs in real time with its Web Application Firewall.
iThemes Security Pro: Goes beyond scanning by preventing brute force logins, blocking known bad bots, enforcing strong passwords, detecting file changes, and offering Two-Factor Authentication.
Combined, these plugins dramatically reduce the attack surface of your WordPress installation.
Alongside plugins, you can scan suspicious files or your entire website using external services:
These tools are free to start with, but professional paid scans provide deeper detection layers. For best results, scan every file before installation – even if it comes from a trusted source.
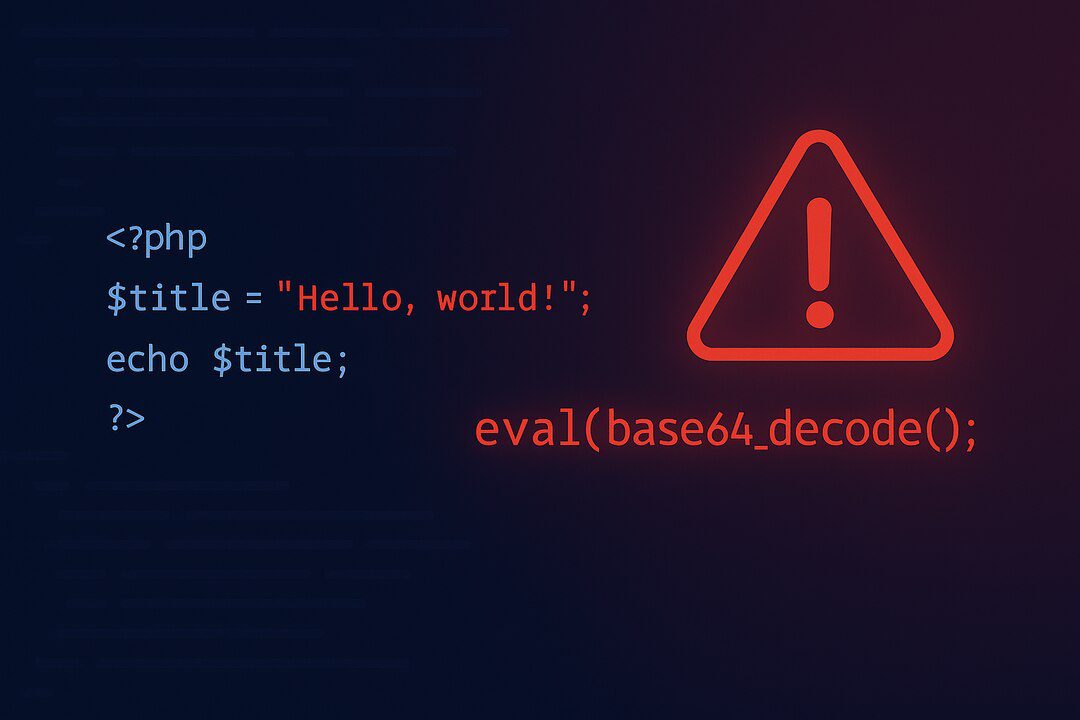
If you’re comfortable with development, manually check for signs of obfuscated or injected code:
eval(), base64_decode(), gzinflate(), and preg_replace() with the /e modifier.document.write() with long encoded strings or suspicious atob() calls.wp-includes/fonts/ containing PHP scripts).While not every occurrence of these functions is malicious, attackers often rely on them to hide backdoors. Compare suspicious files against a clean WordPress installation to verify integrity.
Attackers frequently inject malicious JavaScript into your wp_posts table or alter wp_options to create hidden redirects. Run queries to identify unexpected <script> tags or unfamiliar admin accounts. Always back up your database before making changes. Look for spam links/injected scripts in wp_posts, options like home, siteurl, rogue active_plugins, and suspicious scheduled events:
-- obvious script tags in posts/pages
SELECT ID, post_type, post_status FROM wp_posts
WHERE post_content REGEXP '<script|data:text|atob\\(|unescape\\(' LIMIT 50;
-- siteurl/home integrity
SELECT option_name, option_value FROM wp_options
WHERE option_name IN ('siteurl','home');
-- find odd admin accounts
SELECT ID, user_login, user_email, user_registered FROM wp_users
ORDER BY user_registered DESC LIMIT 10;
If you find suspicious entries, follow this process to remove them safely:
wp db export).siteurl or home values to your actual domain.wp cron event list to detect unusual jobs; remove any that look suspicious.wp-config.php, and ensure proper least-privilege permissions.wp db query, wp user delete).By combining SQL checks, careful manual review, and automated scans, you reduce the risk of hidden reinfection mechanisms inside your database.
Sometimes, the first sign of trouble comes from your visitors. They may report strange popups, redirects, or browser warnings. Always take such feedback seriously, as end users often encounter malicious code that admins overlook.
If Google or Chrome blocks your site for hosting malware, visitors will see a red warning screen. To recover:
Without a full cleanup, your request will be denied, so ensure your site is genuinely malware-free first.
If you discover a compromised site harming users, you can report it to Netcraft’s malware and phishing classification system. This contributes to a safer web ecosystem overall.
Beyond detection, prevention is critical. Apply these measures:
Finally, always download GPL-licensed plugins and themes from trusted marketplaces like DevTools Club Marketplace to avoid hidden malware.
Join our Membership Club
No account yet?
Create an Account